NIAP Certified Secure KVM Switches
Protect Desktops from Cyber Threats with Secure Peripheral Control between Multiple Computers and Devices
Connecting computer peripherals such as keyboard & mouse to a PC introduces potential data leakage and hacking risks. Black Box Secure KVM Switch line provides port isolation between networks ensuring no data is leaked between secure ports and the outside world. Built with true data path isolation between systems and networks, these switches help prevent hardware tampering.
Black Box offers a wide range of NIAP PSD V3.0 certified Secure KVM devices and has currently PSD V.4.0 compliant models und NIAP evaluation. Learn more about the new NIAP Protection Profile and when you should shift to PP V4.0.
Secure KVM Switches Benefits and Features

NIAP Certified Security
Current Secure KVM Switches comply with NIAP PP V.3.0 security certification, equipping them with the high security features that still meet many of today’s Information Assurance safe control standards. We are proud to announce that NIAP has accepted our new range of Secure KVM Switches for evaluation under the latest NIAP PSD V.4.0 protection profile. These new Secure KVM Switches are expected to be among the first that become available with the NIAP PSD V.4.0 certification, meeting the latest cybersecurity requirements from Government.
Improved Operator Situational Awareness with Secure Air-Gap Network Isolation
Control multiple computers through a single keyboard, mouse, and up to four video displays while air-gap maintains absolute isolation between all connected systems.
Largest Secure KVM Switch Portfolio
Black Box offers a wide range of NIAP 3.0 certified Secure KVM Switches suitable for any type of application. Choose from KVM switch models with up to 16-ports, analogue or digital video, single, dual or quad monitors.
Multiple Switching Signals – DVI-I/DisplayPort/HDMI
Monitor systems with the highest analogue or digital resolutions of up to 4K Ultra-HD 3840×2160 @ 30Hz.
Secure Data Transfer without Computer Tampering
Securely transfer files between computers and safeguard your network from accidental transfer, unauthorized access, or compromise of critical data.
True Data Path Isolation
Benefit from hardware-based peripheral isolation with no dependency on firmware, keyboard buffering or memory.
Secure EDID Learn and Video Emulation
Prevent unwanted and unsecure data to be transmitted through the DDC lines by means of secure EDID learning and emulation. The Secure KVM Switches are designed to learn the connected monitor’s EDID upon power up allowing trouble-free connection
to most monitors.
Common Access Card (CAC) reader support
A fully advanced and configurable CAC port supports smart cards or biometric readers. Furthermore, authenticated admins can register and assign specific peripheral devices to the CAC port, allowing users to switch this device along with the KVM
switching of the connected computers.
Network Port Security
Access multiple computers assured that your data is protected from accidental or unauthorized transfer when switching between systems.
Network Isolation
Securely control computers with port to port isolation for secure switching with no port crosstalk.

Air Gap your Network
Achieve air-gap isolation between computing devices with data path isolation, preventing cyber hacking and data leakage in environments where security is critical.
Prevent Data Leakage / Breaches
Block peripheral exploits, data breaches, eavesdropping, computer malware.

Prevent Hardware/ Firmware Tampering
Hardware and firmware tampering by enforcing multilayered security mechanisms.

Prevent Cyber Intrusion
Computers can be catalysts for malicious attack or intellectual property theft. Protect desktop access since your computer or device is a potential point of entry into your network.
| Threat: | Solution: |
|---|
| Microprocessor malfunction or unanticipated software bugs causing data to flow between ports. | Unidirectional data flow is enforced by hardware "data diodes" so data isolation doesn't rely on software integrity. |
| Malicious modification of microprocessor software causing data to leak between ports. | Microprocessors are one-time programmable and soldered on the board. Data isolation does not rely on software; it is ensured by hardware. |
| Detection of signals on one computer by monitoring for crosstalk (leakage) signals on another computer. | No connections to sensitive inputs such as computer microphone ports. Minimum crosstalk separation provided between signals from one computer and input or I/O signals to another. |
| Timing analysis attacks (looking at what happens on one port to determine data flow patterns on another). | Only one computer is connected at a time to any shared circuitry. Links are unidirectional, preventing timing analysis.
|

Mission-focused technology solutions that meet security and compliance standards

Complete solutions for transportation, including DAS/Wi-Fi, cloud and digital signage

Secure, compliant technology solutions and products ideal for public sector agencies

Technology that increases learning, productivity, collaboration and student success

Provide connectivity for medical imaging, remote servers, and patient data access

Banking and Finance
Secure KVM Switch Use Cases
Standard KVM Switching between unclassified computers
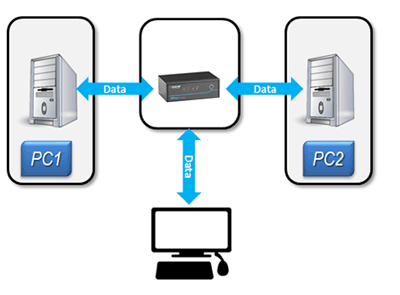
Secure KVM Switching between computers with different security levels
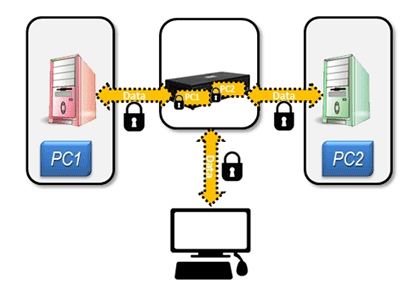
NIAP 3.0 certified Secure KVM Switches provide absolute isolation between networks, ideal for use in defense, intelligence and other applications where sensitive data must be protected by controlling access to classified networks in addition to public networks such as the Internet.
Secure KVM Switches supported Connections
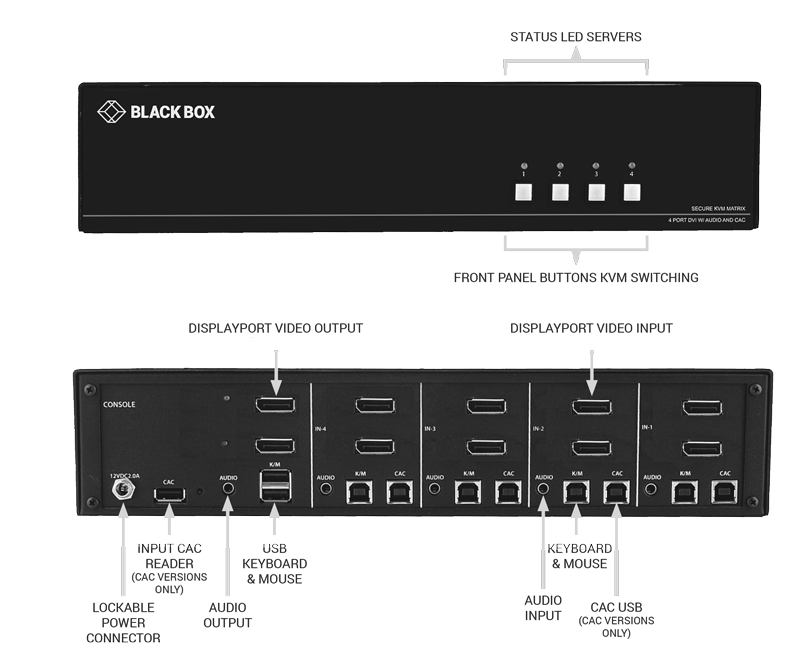
(Example 4-Port dual head DisplayPort KVM Switch)
2/4/8/16-ports with DisplayPort, HDMI, DVI-I, audio, USB and optional CAC USB reader – centralize control of multiple systems for one keyboard-mouse and up to four monitors.
4/8-ports with USB, audio and optional CAC - switch seamlessly between systems with the cursor, while simultaneously viewing all video sources.
Allows multiple users to connect to multiple different computer sources – industry's first ever NIAP 3.0 certified. Choose from 4 to 8 users and up to four different secure computers
4-ports with DVI-I video, audio, USB and CAC – allows users to see up to four different secure sources on a single monitor.
Locks down otherwise unprotected or vulnerable peripherals, blocks malicious attacks and keeps secure networks secure - perfect for conference rooms or existing large scale KVM Matrices.
Choose from DisplayPort, HDMI or DVI cables.